AWS Organizations is a great way to manage the multi-account strategy in your company. It offers ways to consolidate your billing, savings plans, reserved instances etc. It also has ways to manage organizational governance and security using policies. This blog offers a few actionable approaches to use service control policies to prevent costs in the organization.
Eligibility checklist
You can adopt these approaches if:
- AWS Organizations is set up.
- All accounts are linked to the organization.
- You have Administrator access.
- AWS SCP (Service Control Policies) and All Features are enabled within AWS Organizations.
- The current existing policies are within quota.
Region block
Most companies operate in a few regions. Resources may end up being created in the usually unused regions, whether accidentally or due to a security breach. Since these regions are not used, it is likely that you may not find out about the resources’ existence until the bills are reviewed. This SCP ensures that no resources are created in other regions. We can do that by blocking all API calls for unused regions, except if they are for global services.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DenyUnusedRegions",
"Effect": "Deny",
"NotAction": [
"a4b:*",
"acm:*",
"aws-marketplace-management:*",
"aws-marketplace:*",
"aws-portal:*",
"budgets:*",
"ce:*",
"chime:*",
"cloudfront:*",
"config:*",
"cur:*",
"directconnect:*",
"ec2:DescribeRegions",
"ec2:DescribeTransitGateways",
"ec2:DescribeVpnGateways",
"fms:*",
"globalaccelerator:*",
"health:*",
"iam:*",
"importexport:*",
"kms:*",
"mobileanalytics:*",
"networkmanager:*",
"organizations:*",
"pricing:*",
"route53:*",
"route53domains:*",
"s3:GetAccountPublic*",
"s3:ListAllMyBuckets",
"s3:PutAccountPublic*",
"shield:*",
"sts:*",
"support:*",
"trustedadvisor:*",
"waf-regional:*",
"waf:*",
"wafv2:*",
"wellarchitected:*"
],
"Resource": "*",
"Condition": {
"StringNotEquals": {
"aws:RequestedRegion": [
"us-east-1",
"eu-west-1"
]
},
"ArnNotLike": {
"aws:PrincipalARN": [
"arn:aws:iam::*:role/Role1AllowedToBypassThisSCP",
"arn:aws:iam::*:role/Role2AllowedToBypassThisSCP"
]
}
}
}
]
}EBS block
There is absolutely no reason to create new gp2 or io1 volumes. On an individual basis, the volume costs aren’t too high but they add up really quickly and we may end up overpaying by 20%+. This SCP prevents their creation. This should happen only after all the volumes and launch templates have been right-typed.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DenyOldVolumes",
"Effect": "Deny",
"Action": [
"ec2:CreateVolume",
"ec2:RunInstances",
"ec2:RunScheduledInstances"
],
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:VolumeType": [
"gp2","io1"
]
}
}
}
]
}GPU instance block
Unless your organization is running graphics or AI-heavy workloads, it is likely that GPU instances are not being used. GPU instances are expensive and are targets for crypto mining attacks. If you know you don’t need them, it is valuable to prevent their creation. This means all the g series and p series instances should be prevented from launching.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DenyGPUBasedInstances",
"Effect": "Deny",
"Action": [
"ec2:RunInstances",
"ec2:StartInstances"
],
"Resource": [
"arn:aws:ec2:*:*:instance/*"
],
"Condition": {
"StringLike": {
"ec2:InstanceType": [
"p3dn.*",
"p4d.*",
"g*",
"p3.*"
]
}
}
}
]
}Step-by-step fix
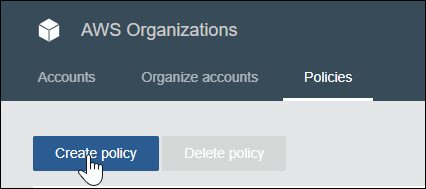
- In the AWS Organizations console, select the Policies tab, and then select Create policy.
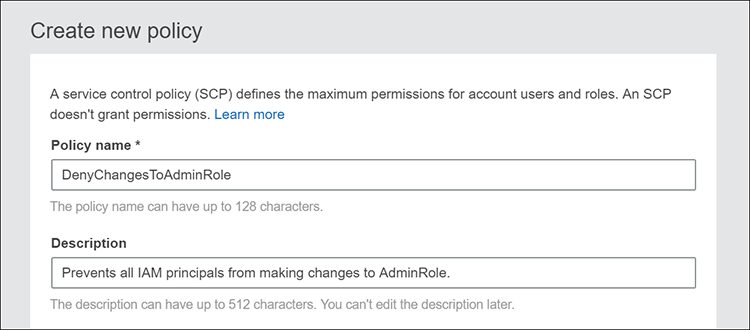
- Give your policy a name and description that will help you quickly identify it.
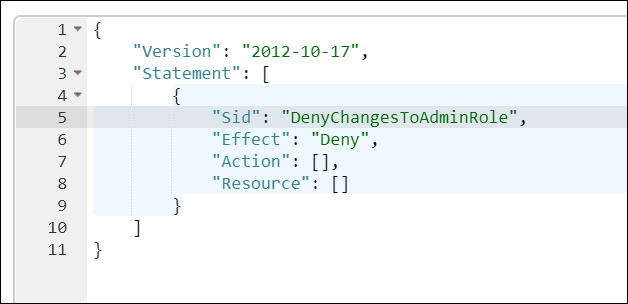
- The policy editor provides you with an empty statement in the text editor to get started. Position your cursor inside the policy statement. Add the appropriate statements from above.
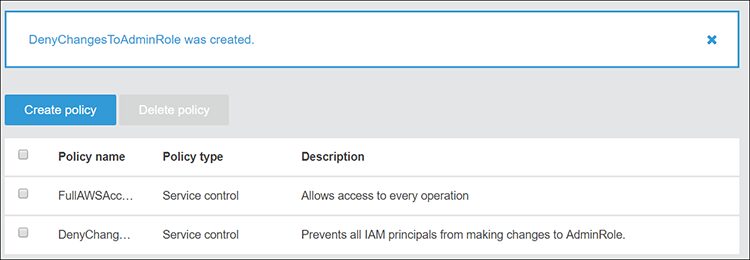
- Select the Save changes button to create your policy. You can see the new policy in the Policies tab.
- Finally, attach the policy to the AWS accounts/OU where you want to apply the permissions.
For easy, automated fixes to optimization opportunities like this and more, check out CloudFix.